拓扑如下图所示:
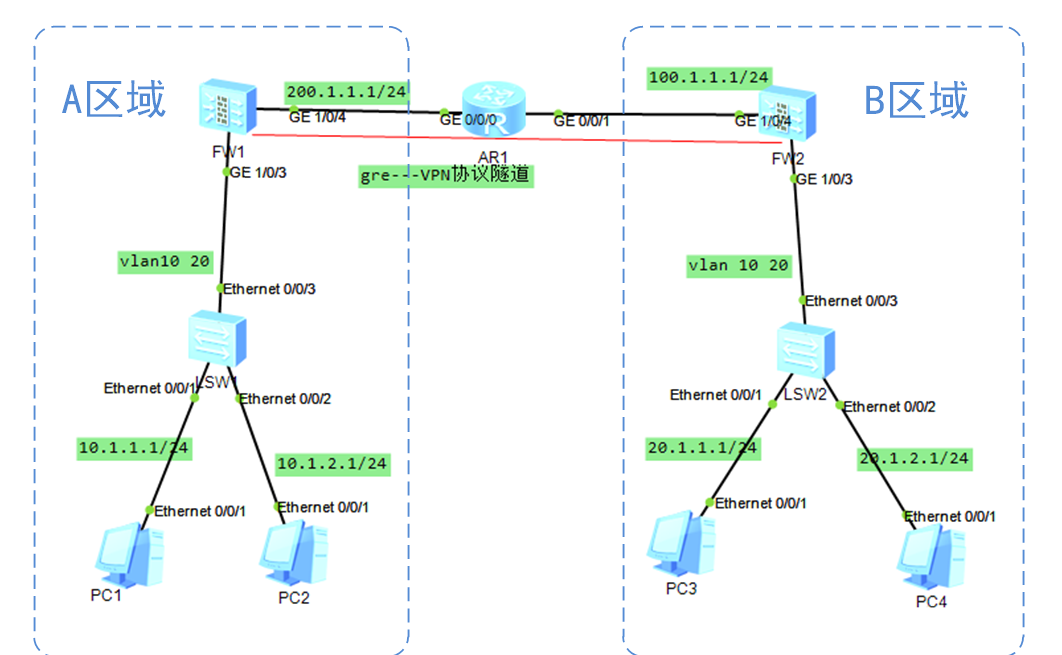
A\B为不同地区的两套网络,需要通过配置GRE实现网络安全连接。
配置步骤如下:
1.配置基本的ip地址
2.配置两台防火墙之间的路由可以到达,采用静态路由配
3.配置防火墙与所属区域内网的域间策略通过
4.配置tunnel 口 ,其中协议为gre协议,源地址为防火墙出口
5.目的地址为另一个防火墙的出口。
6.配置到达对端区域内网的静态路由,下一跳是在tunnel 口上。
具体配置如下:
防火墙FW1:
interface GigabitEthernet1/0/3.1
vlan-type dot1q 10 \\vlan的类型打标签为10
ip address 10.1.1.254 255.255.255.0
ospf network-type p2p \\ospf的网络类型为p2p缩短建立邻居时间
service-manage ping permit
interface GigabitEthernet1/0/3.2
vlan-type dot1q 20
ip address 10.1.2.254 255.255.255.0
ospf network-type p2p
service-manage ping permit
interface GigabitEthernet1/0/4
undo shutdown
ip address 200.1.1.1 255.255.255.0
service-manage ping permit
interface Tunnel0
ip address 172.1.1.1 255.255.255.0
tunnel-protocol gre
source 200.1.1.1
destination 100.1.1.1
firewall zone local
set priority 100
firewall zone trust
set priority 85
add interface GigabitEthernet0/0/0
add interface GigabitEthernet1/0/3
add interface GigabitEthernet1/0/3.1
add interface GigabitEthernet1/0/3.2
firewall zone untrust
set priority 5
add interface GigabitEthernet1/0/4
add interface Tunnel0
静态路由的配置:
ip route-static 20.1.0.0 255.255.0.0 Tunnel0
ip route-static 100.1.1.0 255.255.255.0 200.1.1.2
防火墙的域间策略:
security-policy
rule name t_u
source-zone trust
destination-zone untrust
action permit
rule name u_t
source-zone untrust
destination-zone trust
action permit
rule name l_u
source-zone local
destination-zone untrust
action permit
rule name u_ll
source-zone untrust
destination-zone local
action permit
防火墙FW2配置:
interface GigabitEthernet1/0/3.1
vlan-type dot1q 10
description vl10
ip address 20.1.1.254 255.255.255.0
ospf network-type p2p
service-manage ping permit
interface GigabitEthernet1/0/3.2
vlan-type dot1q 20
description vl20
ip address 20.1.2.254 255.255.255.0
ospf network-type p2p
service-manage ping permit
interface GigabitEthernet1/0/4
undo shutdown
ip address 100.1.1.1 255.255.255.0
service-manage ping permit
tunnel 0的ipv4地址:
interface Tunnel0
ip address 172.1.1.2 255.255.255.0
tunnel-protocol gre
source 100.1.1.1
destination 200.1.1.1
把接口加入防火墙的安全区域:
firewall zone trust
set priority 85
add interface GigabitEthernet0/0/0
add interface GigabitEthernet1/0/3
add interface GigabitEthernet1/0/3.1
add interface GigabitEthernet1/0/3.2
firewall zone untrust
set priority 5
add interface GigabitEthernet1/0/4
add interface Tunnel0
配置到达公网与私网的静态路由:
ip route-static 10.1.0.0 255.255.0.0 Tunnel0
ip route-static 200.1.1.0 255.255.255.0 100.1.1.2
配置防火墙的域间策略:
security-policy
rule name t_u
source-zone trust
destination-zone untrust
action permit
rule name u_t
source-zone untrust
destination-zone trust
action permit
rule name l_u
source-zone local
destination-zone untrust
action permit
rule name u_ll
source-zone untrust
destination-zone local
action permit